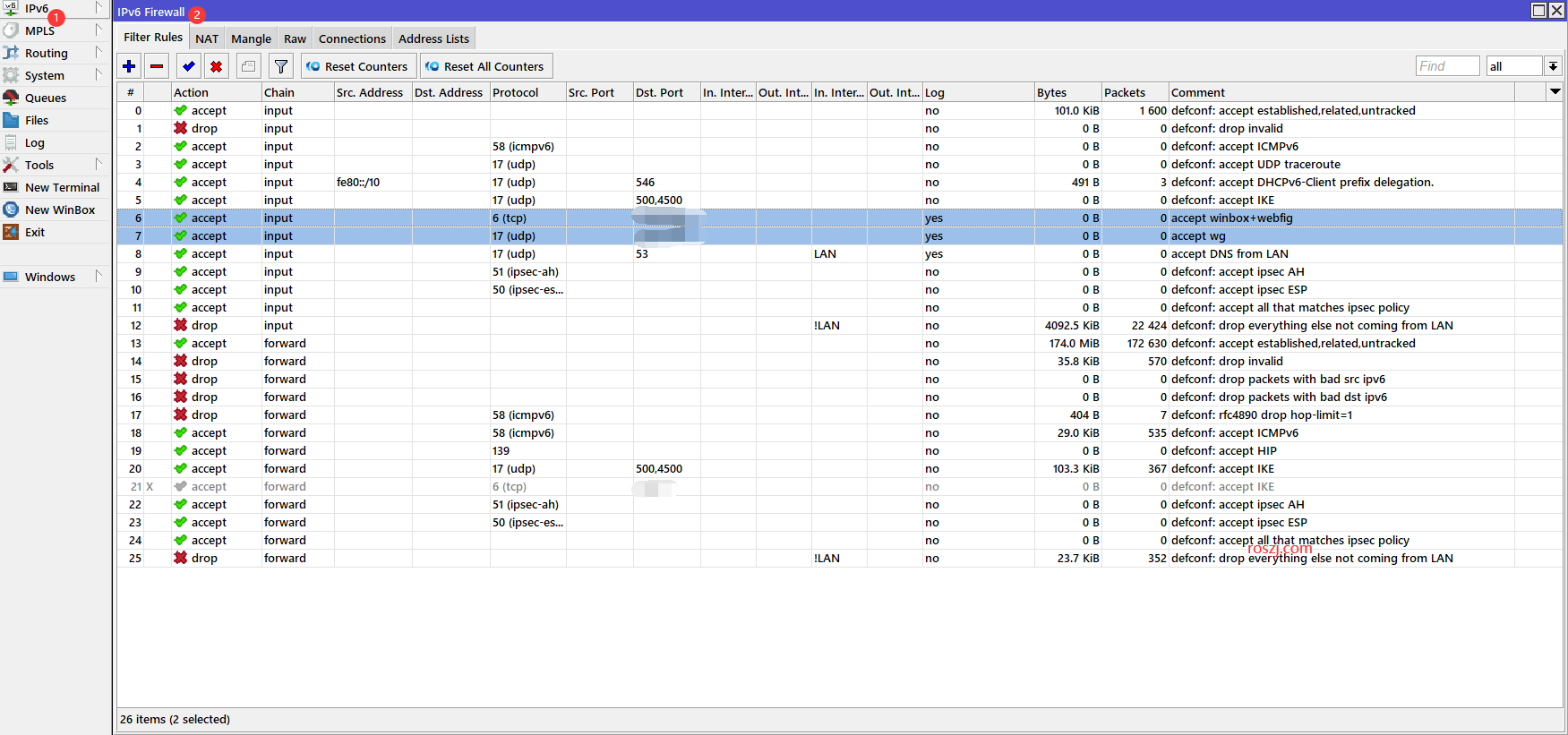
上一篇mikrotik ipv6开启后,意味着内网的所有设备已经全端口开放在公网。这一篇提供一份脚本,来解决安全问题。
这个防火墙脚本的核心功能是增强IPv6网络的安全性,具体分为以下几个方面:
- 定义和标记“无效”IPv6地址:
- 使用
address-list将常见的无效、保留或专用IPv6地址(例如::1、fec0::/10等)添加到bad_ipv6列表,以便后续规则直接引用。
- 使用
- 输入链(Input Chain)规则:
- 允许特定流量:
- 接受已建立或相关的连接(如ESTABLISHED、RELATED)。
- 接受有效的ICMPv6流量、UDP路由跟踪和DHCPv6客户端流量。
- 开放特定管理端口(Winbox、Webfig)和DNS服务。
- 接受IPSec相关协议和策略匹配的流量。
- 拒绝非法或异常流量:
- 丢弃无效连接和来自非局域网(LAN)的其他流量。
- 允许特定流量:
- 转发链(Forward Chain)规则:
- 允许特定流量:
- 接受已建立或相关的连接,ICMPv6流量,IPSec协议及策略匹配的流量。
- 丢弃非法或异常流量:
- 丢弃源地址或目标地址为
bad_ipv6列表的流量。 - 拒绝ICMPv6跳数限制为1的流量(RFC 4890)。
- 阻止未通过目标地址转换(dstnat)且不来自局域网的其他流量。
- 丢弃源地址或目标地址为
- 允许特定流量:
- 全局安全策略:
- 确保防火墙的默认策略是“拒绝除明确允许之外的所有流量”,从而减少未授权访问的可能性。
简要结论:
该脚本通过定义无效地址列表、允许合法的IPv6协议和管理流量,同时丢弃异常流量,实现了全面的IPv6防火墙安全配置。
/ipv6 firewall address-list
add address=::/128 comment="defconf: unspecified address" list=bad_ipv6
add address=::1/128 comment="defconf: lo" list=bad_ipv6
add address=fec0::/10 comment="defconf: site-local" list=bad_ipv6
add address=::ffff:0.0.0.0/96 comment="defconf: ipv4-mapped" list=bad_ipv6
add address=::/96 comment="defconf: ipv4 compat" list=bad_ipv6
add address=100::/64 comment="defconf: discard only " list=bad_ipv6
add address=2001:db8::/32 comment="defconf: documentation" list=bad_ipv6
add address=2001:10::/28 comment="defconf: ORCHID" list=bad_ipv6
add address=3ffe::/16 comment="defconf: 6bone" list=bad_ipv6
add address=::224.0.0.0/100 comment="defconf: other" list=bad_ipv6
add address=::127.0.0.0/104 comment="defconf: other" list=bad_ipv6
add address=::/104 comment="defconf: other" list=bad_ipv6
add address=::255.0.0.0/104 comment="defconf: other" list=bad_ipv6
/ipv6 firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=input comment="defconf: accept UDP traceroute" port=\
33434-33534 protocol=udp
add action=accept chain=input comment=\
"defconf: accept DHCPv6-Client prefix delegation." dst-port=546 protocol=\
udp src-address=fe80::/10
add action=accept chain=input comment="defconf: accept IKE" dst-port=500,4500 \
protocol=udp
#放行winbox和网页管理入口和其它intput端口的白名单
add action=accept chain=input comment="accept winbox+webfig" dst-port=\
8291,80 log=yes protocol=tcp
add action=accept chain=input comment="accept wg" dst-port=3003,3005 log=yes \
protocol=udp
add action=accept chain=input comment="accept DNS from LAN" dst-port=53 \
in-interface-list=LAN log=yes protocol=udp
add action=accept chain=input comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=input comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=input comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=input comment=\
"defconf: drop everything else not coming from LAN" in-interface-list=\
!LAN
add action=accept chain=forward comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop packets with bad src ipv6" src-address-list=bad_ipv6
add action=drop chain=forward comment=\
"defconf: drop packets with bad dst ipv6" dst-address-list=bad_ipv6
add action=drop chain=forward comment="defconf: rfc4890 drop hop-limit=1" \
hop-limit=equal:1 protocol=icmpv6
add action=accept chain=forward comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=forward comment="defconf: accept HIP" protocol=139
add action=accept chain=forward comment="defconf: accept IKE" dst-port=\
500,4500 protocol=udp
add action=accept chain=forward comment="defconf: accept IKE" disabled=yes \
dst-port=3389 protocol=tcp
add action=accept chain=forward comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=forward comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=forward comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=forward comment=\
"defconf: drop everything else not coming from LAN" connection-nat-state=\
!dstnat in-interface-list=!LAN